
Allison Bishop delivers TEDx talk
In a retelling of Alice in Wonderland, Bishop illustrates the fundamentals and power of cryptography while warning how human error undermines that power.

In a retelling of Alice in Wonderland, Bishop illustrates the fundamentals and power of cryptography while warning how human error undermines that power.

“For the development of statistical learning theory, the theoretical foundations for machine learning, and support vector machines,” Vladimir Vapnik … Continue reading Vladimir Vapnik awarded the IEEE John von Neumann Medal

Technique models geometry of individual hair strands to predict how soft, curly hair will react to a character’s motions or the external forces of wind and water.

It describes how to coordinate communication among ultra-low power devices (e.g., Internet of things) that must operate under stringent power constraints to maximize throughput rates among these devices.

Part 1: Liberal arts students and computer science. The flow of liberal arts students into computer science is forcing changes … Continue reading Making computer science accessible to Columbia’s wider student population

Study coauthored by David Blei and published in Nature Genetics describes using TeraStructure, an algorithm capable of analyzing up to 1 million genomes, to infer ancestral makeup of 10,000 individuals.

Floraform, a design system from Nervous System, simulates differentially growing elastic surfaces to craft unique 3D-printed jewelry.

They will build a system to detect outages by monitoring flow of out-of-band data (Twitter feeds, communications networks) so outages can be detected even if grid monitoring system is disabled.

The site, which harnesses donated genetic test results for scientific research, has new features and is already working with the National Breast Cancer Coalition.

In podcast, Stolfo discusses current and future uses of artificial intelligence to detect security intrusions.
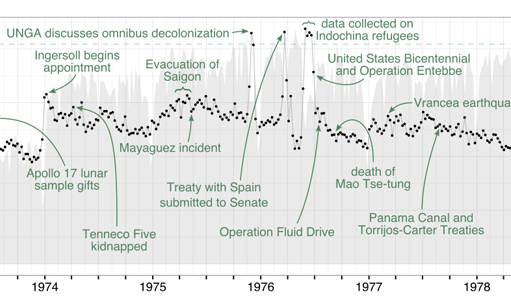
Paper by David Blei, Allison J. B. Chaney, Hanna Wallach, and Matthew Connelly describes using a Bayesian modeling technique to characterize and isolate significant events in 2M US diplomatic cables from the 1970s.

Paper led by Yaniv Erlich describes storing 2.1Mbytes in synthetic DNA molecules, copying data multiple times using biochemical reactions info, later retrieving info without a single error.

For the lasting impact of contributions in furthering the theory or development of secure systems, Steven M. Bellovin has been … Continue reading Steven Bellovin is this year’s recipient of the ESORICS Outstanding Research Award

Second prize is for combating VR sickness by subtly modifying the field of view, and an honorable mention is for a technique to show wearers of head-worn displays how to rotate a 3D object.

“Turn-taking cues in task-oriented dialogue” is named by International Speech and Communications Association as best paper published in Computer Speech and Language, 2011–2015.
Find open faculty positions here.
President Bollinger announced that Columbia University along with many other academic institutions (sixteen, including all Ivy League universities) filed an amicus brief in the U.S. District Court for the Eastern District of New York challenging the Executive Order regarding immigrants from seven designated countries and refugees. Among other things, the brief asserts that “safety and security concerns can be addressed in a manner that is consistent with the values America has always stood for, including the free flow of ideas and people across borders and the welcoming of immigrants to our universities.”
This recent action provides a moment for us to collectively reflect on our community within Columbia Engineering and the importance of our commitment to maintaining an open and welcoming community for all students, faculty, researchers and administrative staff. As a School of Engineering and Applied Science, we are fortunate to attract students and faculty from diverse backgrounds, from across the country, and from around the world. It is a great benefit to be able to gather engineers and scientists of so many different perspectives and talents – all with a commitment to learning, a focus on pushing the frontiers of knowledge and discovery, and with a passion for translating our work to impact humanity.
I am proud of our community, and wish to take this opportunity to reinforce our collective commitment to maintaining an open and collegial environment. We are fortunate to have the privilege to learn from one another, and to study, work, and live together in such a dynamic and vibrant place as Columbia.
Sincerely,
Mary C. Boyce
Dean of Engineering
Morris A. and Alma Schapiro Professor