With $2.5M ONR grant, Suman Jana to lead broad research effort to secure cyber-physical systems

The Office of Naval Research (ONR) has awarded a three-year, $2.5M grant to three Columbia University researchers to build a security architecture to protect cyber-physical systems (CPSs) from failures and cyber-attacks. Suman Jana will lead the research effort, working with Salvatore Stolfo and Simha Sethumadhavan, each of whom will oversee a particular aspect of the architecture. All three are Columbia University computer scientists working in the area of security.
The large grant amount reflects the growing need to harden CPSs. Similar to embedded systems, CPSs encompass a wide number and variety of devices and sensors as well as the underlying software, communications, and networks that link components. What distinguishes CPSs from embedded systems is the tight coupling between computing resources—the cyber space—and the physical environment. At the heart of CPSs are sensors that take readings of the physical environment and relay the data to other components that monitor this data or act on it in some way.
A large ship with steering and engine control, electric power, hydraulics, and other systems that respond to real-time input from the environment is a prime example of a CPS. Other systems that can qualify as CPSs—depending on the degree to which they merge the cyber and physical worlds—are the Internet of Things, smart grids, autonomous airline and automobile systems, medical monitoring, and robotics systems.
Securing CPSs poses special challenges. Says Jana, “CPS systems often contain a large number of diverse, resource-constrained, and physically distributed components. The resource-constrained nature of the components makes it harder to run heavyweight security software while the physically distributed nature makes it easier for the attacker to compromise a component by either damaging or replacing it with one of its own.”
Such a large, complex attack surface is one security concern; another is the redundancy built into CPSs to ensure that the failure of a single component does not affect critical systems; from a security perspective, this redundancy means having to secure not a single component but all other components that replicate its function.
However, the redundancy meant for fault tolerance may also be key to preventing malicious attacks. With BUDDY, a security architecture being designed for CPSs, Jana and his colleagues propose leveraging existing redundancy to increase the amount of data shared among components so that, like buddies in a buddy system, components can more closely monitor one another for signs any are under attack. For example, rather than crosscheck only final results as is done now, BUDDY would randomly compare intermediate results as well, thus preventing sophisticated attacks that might otherwise avoid detection by making the output look correct.
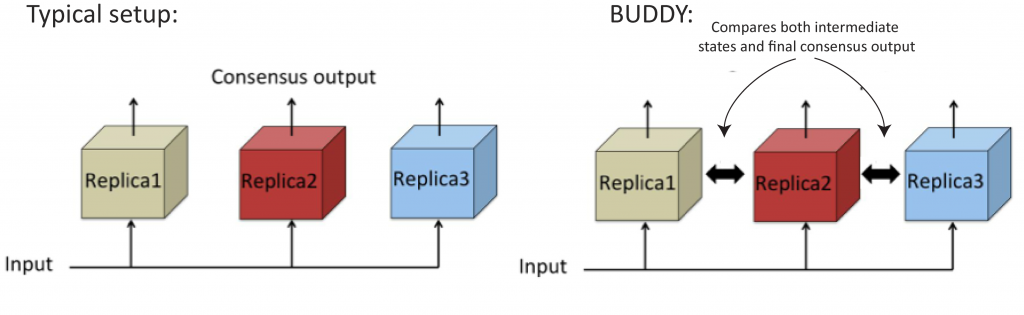 More data, same structure. Rather than checking only final computations, BUDDY (randomly) compares intermediate computations among components to detect and report intrusions. This buddy approach works for checking run-time software and hardware processes and during software development to prevent bugs.
More data, same structure. Rather than checking only final computations, BUDDY (randomly) compares intermediate computations among components to detect and report intrusions. This buddy approach works for checking run-time software and hardware processes and during software development to prevent bugs.
Having components more closely monitor one another also distributes the security task, removing a single point of failure. Any attacker is faced with the difficult task of simultaneously attacking many components.
More data results from comparing many intermediate states of redundant components, and one key requirement of BUDDY, according to Jana, will be managing the data overhead without impairing performance. “By performing most checks asynchronously, without blocking the main execution path, computations will be able to proceed in parallel with the checks.”
Comparing intermediate computations is only one aspect of BUDDY, which will use redundancy across three levels of security: (1) runtime monitoring of software for malicious activity, (2) runtime monitoring of hardware to detect backdoors and supply chain attacks, and (3) detecting bugs during software development to prevent vulnerabilities that can later be exploited by attackers.
This last level is the responsibility of Jana, who will automatically extract error specifications by running multiple programs that provide similar functionality and observing the common ways the programs function. “As long as the majority of the redundant components are not buggy in the same way, one can compare their behaviors for the same inputs and infer the behavior demonstrated by the majority of components to be the correct specification. Specifications captured in this way can then be used to automatically find bugs.” It’s a scalable technique that frees developers from the tedious and error-prone task of manually writing specifications.
While specification mining has not previously been used in CPSs, it fits in well with BUDDY’s overall approach of looking at existing redundancies for ways to insert new protections. Redundancy is both the means to build security mechanisms within a CPS and what makes it possible to deploy in such large, distributed systems. “The nice thing about leveraging redundancy in a CPS is that you don’t have to change the system that much to add security.” The redundancy needed for security is already there.
– Linda Crane,
Posted 11/17/2016

