Wireless and Networking

Neural network applications have become popular in both enterprise and personal settings. Network solutions are tuned meticulously for each task, and designs that can robustly resolve queries end up in high demand. As the commercial value of accurate and performant machine learning models increases, so too does the demand to protect neural architectures as confidential investments. We explore the vulnerability of neural networks deployed as black boxes across accelerated hardware through electromagnetic side channels. We examine the magnetic flux emanating from a graphics processing unit's power cable, as acquired by a cheap $3 induction sensor, and find that this signal betrays the detailed topology and hyperparameters of a black-box neural network model. The attack acquires the magnetic signal for one query with unknown input values, but known input dimensions. The network reconstruction is possible due to the modular layer sequence in which deep neural networks are evaluated. We find that each layer component's evaluation produces an identifiable magnetic signal signature, from which layer topology, width, function type, and sequence order can be inferred using a suitably trained classifier and a joint consistency optimization based on integer programming. We study the extent to which network specifications can be recovered, and consider metrics for comparing network similarity. We demonstrate the potential accuracy of this side channel attack in recovering the details for a broad range of network architectures, including random designs. We consider applications that may exploit this novel side channel exposure, such as adversarial transfer attacks. In response, we discuss countermeasures to protect against our method and other similar snooping techniques.

Zhao Tian, Yu-Lin Wei, Wei-Nin Chang, Xi Xiong, Changxi Zheng, Hsin-Mu Tsai, Kate Ching-Ju Lin, and Xia Zhou
Augmenting Indoor Inertial Tracking with Polarized Light.
Conference on Mobile Systems, Applications, and Services (MobiSys), 2018
Paper (PDF) Abstract Bibtex
Augmenting Indoor Inertial Tracking with Polarized Light.
Conference on Mobile Systems, Applications, and Services (MobiSys), 2018
Paper (PDF) Abstract Bibtex
Inertial measurement unit (IMU) has long suffered from the problem
of integration drift, where sensor noises accumulate quickly and
cause fast-growing tracking errors. Existing methods for calibrating
IMU tracking either require human in the loop, or need energyconsuming
cameras, or suffer from coarse tracking granularity. We
propose to augment indoor inertial tracking by reusing existing
indoor luminaries to project a static light polarization pattern in the
space. This pattern is imperceptible to human eyes and yet through
a polarizer, it becomes detectable by a color sensor, and thus can
serve as fine-grained optical landmarks that constrain and correct
IMU's integration drift and boost tracking accuracy. Exploiting
the birefringence optical property of transparent tapes -- a lowcost
and easily-accessible material -- we realize the polarization
pattern by simply adding to existing light cover a thin polarizer
film with transparent tape stripes glued atop. When fusing with
IMU sensor signals, the light pattern enables robust, accurate and
low-power motion tracking. Meanwhile, our approach entails low
deployment overhead by reusing existing lighting infrastructure
without needing an active modulation unit. We build a prototype of
our light cover and the sensing unit using off-the-shelf components.
Experiments show 4.3 cm median error for 2D tracking and 10 cm
for 3D tracking, as well as its robustness in diverse settings.
@inproceedings{Tian2018AII,
author = {Tian, Zhao and Wei, Yu-Lin and Chang, Wei-Nin and Xiong, Xi and Zheng, Changxi and
Tsai, Hsin-Mu and Lin, Kate Ching-Ju and Zhou, Xia},
title = {Augmenting Indoor Inertial Tracking with Polarized Light},
booktitle = {Proceedings of the 16th Annual International Conference on Mobile Systems,
Applications, and Services},
series = {MobiSys '18},
year = {2018},
numpages = {14},
publisher = {ACM},
address = {New York, NY, USA},
}
Zhao Tian, Yu-Lin Wei, Xi Xiong, Wei-Nin Chang, Hsin-Mu Tsai, Kate Ching-Ju Lin, Changxi Zheng, and Xia Zhou
Position: Augmenting Inertial Tracking with Light.
Visible Light Communication Systems (VLCS), 2017
Paper (PDF) Bibtex
Position: Augmenting Inertial Tracking with Light.
Visible Light Communication Systems (VLCS), 2017
Paper (PDF) Bibtex
@inproceedings{Tian:2017:PAI,
author = {Tian, Zhao and Wei, Yu-Lin and Xiong, Xi and Chang, Wei-Nin and Tsai, Hsin-Mu and Lin,
Kate Ching-Ju and Zheng, Changxi and Zhou, Xia},
title = {Position: Augmenting Inertial Tracking with Light},
booktitle = {Proceedings of the 4th ACM Workshop on Visible Light Communication Systems},
series = {VLCS '17},
year = {2017},
location = {Snowbird, Utah, USA},
pages = {25--26},
numpages = {2},
publisher = {ACM}
}
Xi Xiong, Justin Chan, Ethan Yu, Nisha Kumari, Ardalan Amiri Sani, Changxi Zheng, and Xia Zhou
Customizing Indoor Wireless Coverage via a 3D-Fabricated Reflector.
ACM Systems for Energy-Efficient Built Environments (BuildSys), 2017
Paper (PDF) Project Page Abstract Video
Customizing Indoor Wireless Coverage via a 3D-Fabricated Reflector.
ACM Systems for Energy-Efficient Built Environments (BuildSys), 2017
Paper (PDF) Project Page Abstract Video
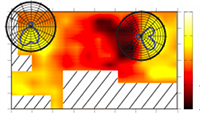
Judicious control of indoor wireless coverage is crucial in built environments. It enhances signal reception, reduces harmful interference, and raises the barrier for malicious attackers. Existing methods are either costly, vulnerable to attacks, or hard to configure. We present a low-cost, secure, and easy-to-configure approach that uses an easily-accessible, 3D-fabricated reflector to customize wireless coverage. With input on coarse-grained environment setting and preferred coverage (e.g., areas with signals to be strengthened or weakened), the system computes an optimized reflector shape tailored to the given environment. The user simply 3D prints the reflector and places it around a Wi-Fi access point to realize the target coverage. We conduct experiments to examine the efficacy and limits of optimized reflectors in different indoor settings. Results show that optimized reflectors coexist with a variety of Wi-Fi APs and correctly weaken or enhance signals in target areas by up to 10 or 6 dB, resulting to throughput changes by up to -63.3% or 55.1%.

Justin Chan, Changxi Zheng, and Xia Zhou
3D Printing Your Wireless Coverage.
ACM Workshop on Hot Topics in Wireless (HotWireless), 2015
(Hot Paper Award)
Paper (PDF) Abstract Video Bibtex
3D Printing Your Wireless Coverage.
ACM Workshop on Hot Topics in Wireless (HotWireless), 2015
(Hot Paper Award)
Paper (PDF) Abstract Video Bibtex
Directing wireless signals and customizing wireless coverage is of great importance in residential, commercial, and industrial environments. It can improve the wireless reception quality, reduce the energy consumption, and achieve better security and privacy. To this end, we propose WiPrint, a new computational approach to control wireless coverage by mounting signal reflectors in carefully optimized shapes on wireless routers. Leveraging 3D reconstruction, fast-wave simulations in acoustics, computational optimization, and 3D fabrication, our method is low-cost, adapts to different wireless routers and physical environments, and has a far-reaching impact by interweaving computational techniques to solve key problems in wireless communication.
@inproceedings{Chan2015,
author = {Chan, Justin and Zheng, Changxi and Zhou, Xia},
title = {3D Printing Your Wireless Coverage},
booktitle = {Proceedings of the 2nd International Workshop on Hot Topics in Wireless},
series = {HotWireless '15},
year = {2015},
pages = {1--5},
numpages = {5},
publisher = {ACM},
address = {New York, NY, USA}
}
Changxi Zheng, Lusheng Ji, Dan Pei, Jia Wang and Paul Francis
A Light-Weight Distributed Scheme for Detecting IP Prefix Hijacks in Real-time.
ACM SIGCOMM, Kyoto, Japan, August 2007
Paper (PDF) Abstract Bibtex
A Light-Weight Distributed Scheme for Detecting IP Prefix Hijacks in Real-time.
ACM SIGCOMM, Kyoto, Japan, August 2007
Paper (PDF) Abstract Bibtex
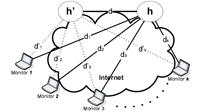
As more and more Internet IP prefix hijacking incidents are being reported, the value of hijacking detection services has become evident. Most of the current hijacking detection approaches monitor IP prefixes on the control plane and detect inconsistencies in route advertisements and route qualities. We propose a different approach that utilizes information collected mostly from the data plane. Our method is motivated by two key observations: when a prefix is not hijacked, 1) the hop count of the path from a source to this prefix is generally stable; and 2) the path from a source to this prefix is almost always a super-path of the path from the same source to a reference point along the previous path, as long as the reference point is topologically close to the prefix. By carefully selecting multiple vantage points and monitoring from these vantage points for any departure from these two observations, our method is able to detect prefix hijacking with high accuracy in a light-weight, distributed, and real-time fashion. Through simulations constructed based on real Internet measurement traces, we demonstrate that our scheme is accurate with both false positive and false negative ratios below 5%.
@inproceedings{Zheng:2007,
author = {Zheng, Changxi and Ji, Lusheng and Pei, Dan and Wang, Jia and Francis, Paul},
title = {A light-weight distributed scheme for detecting ip prefix hijacks in real-time},
booktitle = {Proceedings of the 2007 conference on Applications, technologies,
architectures, and protocols for computer communications},
series = {SIGCOMM '07},
year = {2007},
location = {Kyoto, Japan},
pages = {277--288},
numpages = {12},
publisher = {ACM},
address = {New York, NY, USA},
}Guobin Shen, Changxi Zheng, Wei Pu and Shipeng Li
Distributed Segment Tree: A Unified Architecture to Support Range Query and Cover Query.
Technical Report MSR-TR-2007-30, 2007
Paper (PDF)
Distributed Segment Tree: A Unified Architecture to Support Range Query and Cover Query.
Technical Report MSR-TR-2007-30, 2007
Paper (PDF)
Changxi Zheng, Guobin Shen, Shipeng Li, and Scott Shenker
Distributed Segment Tree: Support of Range Query and Cover Query over DHT.
The 5th International Workshop on Peer-to-Peer Systems (IPTPS) Santa Barbara, US, February 2006
Paper (PDF) Abstract Bibtex
Distributed Segment Tree: Support of Range Query and Cover Query over DHT.
The 5th International Workshop on Peer-to-Peer Systems (IPTPS) Santa Barbara, US, February 2006
Paper (PDF) Abstract Bibtex
Range query, which is defined as to find all the keys in a certain
range over the underlying P2P network, has received a lot of
research attentions recently. However, cover query, which is to
find all the ranges currently in the system that cover a given key,
is rarely touched. In this paper, we first identify that cover query
is a highly desired functionality by some popular P2P applications,
and then propose distributed segment tree (DST), a layered DHT
structure that incorporates the concept of segment tree. Due to
the intrinsic capability of segment tree in maintaining the sturcture
of ranges, DST is shown to be very efficient for supporting both
range query and cover query in a uniform way. It also possesses
excellent parallelizability in query operations and can achieve O(1)
complexity for moderate query ranges. To balance the load among
DHT nodes, we design a downward load stripping mechanism that
controls tradeoffs between load and performance. We implemented
DST on publicly available OpenDHT service and performed extensive
real experiments. All the results and comparisons demonstrate
the effectiveness of DST for several important metrics.
@inproceedings{Zheng06DST,
author = {Changxi Zheng and Guobin Shen and Shipeng Li and Scott Shenker},
title = {Distributed segment tree: Support of range query and cover query over dht},
booktitle = {In proceedings of the 5th International Workshop on
Peer-to-Peer Systems (IPTPS 06)},
year = {2006}
}Ke Liang, Zaoyang Gong, Changxi Zheng, and Guobin Shen
MOVIF: A Lower Power Consumption Live Video Multicasting Framework over Ad-hoc Networks with Terminal Collaboration.
International Symposium on Intelligent Signal Processing and Communication Systems (ISPACS), Hong Kong, December 2005
Paper (PDF) Abstract
MOVIF: A Lower Power Consumption Live Video Multicasting Framework over Ad-hoc Networks with Terminal Collaboration.
International Symposium on Intelligent Signal Processing and Communication Systems (ISPACS), Hong Kong, December 2005
Paper (PDF) Abstract
Live video multicasting over wireless ad hoc networks is a tough
problem due to the restricted computational ability of the mobile
devices and non-predictive networks status. In this paper,
we propose MoViF, a lower power consumption multicasting framework
for live video multicasting over ad-hoc networks. The proposed
MoViF adopts distributed video coding (DVC) scheme and, as a
result, enjoys all the beneï¬ts of DVC such as lightweight encoder
and built-in error resilient capability. Moreover, MoViF manages
to apply an elegant strategy to minimize the overall power consumption
for all the receivers while improving their decoding quality by
dynamically assign the tasks of aid information extraction to
some intermediate powerful nodes in the multicast tree.
Simulation results demonstrate that the optimal strategy can lower down
the overall power consumption comparing to the random strategy.
Changxi Zheng, Guobin Shen, and Shipeng Li
Distributed Prefetching Scheme for Random Seek Support in Peer-to-Peer Streaming Applications.
Workshop on Advances in Peer-to-Peer Multimedia Streaming, ACM Multimedia 2005, Singapore, November 2005
Paper (PDF) Abstract Bibtex
Distributed Prefetching Scheme for Random Seek Support in Peer-to-Peer Streaming Applications.
Workshop on Advances in Peer-to-Peer Multimedia Streaming, ACM Multimedia 2005, Singapore, November 2005
Paper (PDF) Abstract Bibtex
Through analysis of large volume of user behavior logs during
playing multimedia streaming, we extract a user viewing
pattern. The pattern indicates that random seek is a pervasive phenomenon,
contrary to the common assumptions that
users would watch a video session sequentially and passively
in most works on peer-to-peer streaming. We propose to use efficient
prefetching to facilitate the random seek functionality.
Because of the statistical nature of the user viewing
pattern and the ignorance of the users to the content, we
argue that the pattern should be used as a guidance to the
random seek. Based on the pattern, we set up an analogy
between the optimization problem of minimizing the seeking
distance and the optimal scalar quantization problem. We
then propose an optimal prefetching scheduling algorithm
based on the optimal scalar quantization theory. We further
propose a hierarchical prefetching scheme to carry out
the prefetching more effectively. Real user viewing logs are
used to drive the simulations which demonstrate that the
proposed prefetching scheduling algorithm and the hierarchical
prefetching scheme can improve the seeking performance significantly.
@inproceedings{zheng2005distributed,
title={Distributed prefetching scheme for random seek support in peer-to-peer
streaming applications},
author={Zheng, Changxi and Shen, Guobin and Li, Shipeng},
booktitle={Proceedings of the ACM workshop on Advances in peer-to-peer multimedia streaming},
pages={29--38},
year={2005},
}Changxi Zheng, Guobin Shen, and Shipeng Li
Segment Tree Based Control Plane Protocol for Peer-to-Peer On-Demand Streaming Service Discovery.
Proc. of Visual Communication and Image Processing (VCIP), Beijing, China, July 2005
Paper (PDF) Abstract Bibtex
Segment Tree Based Control Plane Protocol for Peer-to-Peer On-Demand Streaming Service Discovery.
Proc. of Visual Communication and Image Processing (VCIP), Beijing, China, July 2005
Paper (PDF) Abstract Bibtex
As the intense academic interest in video streaming over peer-to-peer(P2P)
network, more and more streaming protocols have been proposed to address
different problems on this field, such as QoS, load balancing, transmission
reliability, bandwidth efficiency, etc. However, to the best of our knowledge, an
important component of any practical P2P streaming system, the streaming
service discovery, is rarely granted particular considerations, which is to
discover potential peers from which a newcomer could receive the requested
stream. In this paper, we are inspired from a special data structure, named
Segment Tree(ST), and propose a protocol to address this problem specifically.
Furthermore, we fully decouple the control plane and data plane on video
streaming, and hence provide more flexibilities in designing protocols on both
of them.
@inproceedings{Zheng05VCIP,
author = {Changxi Zheng and Guobin Shen and Shipeng Li},
title = {Segment Tree Based Control Plane Protocol for Peer-to-Peer
On-Demand Streaming Service Discovery},
booktitle = {In proceedings of Visual Communication and Image Processing (VCIP)},
year = {2006}
}Changxi Zheng, Guobin Shen, Shipeng Li and Qianni Deng
Joint Sender/Receiver Optimization Algorithm for Multi-Path Video Streaming Using High Rate Erasure Resilient Code.
Proc. of IEEE International Conference on Multimedia and Expo (ICME), Amsterdam, Netherlands, July 2005
Paper (PDF) Abstract Bibtex
Joint Sender/Receiver Optimization Algorithm for Multi-Path Video Streaming Using High Rate Erasure Resilient Code.
Proc. of IEEE International Conference on Multimedia and Expo (ICME), Amsterdam, Netherlands, July 2005
Paper (PDF) Abstract Bibtex
In this paper we present a joint sender/receiver optimization algorithm and a
seamless rate adjustment protocol to reduce the total number of packets over
different paths in a streaming framework with a variety of constraints such as
target throughput, dynamic packet loss ratio, and available bandwidths. We
exploit the high rate erasure resilient code for the ease of packet loss
adaption and seamless rate adjustment. The proposed algorithm and adjustment
protocol can be applied at an arbitrary scale. Simulation results demonstrate
that the overall traffic is significantly reduced with the proposed algorithm
and protocol.
@inproceedings{Zheng05ICME,
author = {Changxi Zheng and Guobin Shen and Shipeng Li and Qianni Deng},
title = {Joint Sender/Receiver Optimization Algorithm for Multi-Path Video Streaming
Using High Rate Erasure Resilient Code},
booktitle = {IEEE International Conference on Multimedia and Expo (ICME)},
month = July,
year = {2005}
} Loading ......
COPYRIGHT 2012-2018. ALL RIGHTS RESERVED.
