Security and Usability: Windows Vista
There’s an AP wire story about some of the problems and issues some people have with Windows Vista. Most of the problems are — and were — quite predictable. Some applications don’t work with it, device drivers haven’t always been updated, etc. This sort of issue is neither new nor surprising.
In a similar vein, the article discusses business’ hesitance to upgrade yet:
Before the business version of Vista landed late last year, a Forrester survey of about 1,600 companies found that 31 percent planned to upgrade within a year, and 22 percent more planned to be running it within two years.That section conflates two different issues, application compatibility and OS bugginess. Again, this isn’t new. Sometimes, applications rely on things they shouldn’t have relied on; in this case, that was often the insecurity of older operating systems. In fact, some researchers developed a special tool to help figure out why applications need too many privileges. Naturally, businesses want to wait until their crucial applications work before they upgrade. Bugginess isn’t new, either; I learned more than 35 years ago to "never install .0 of anything".Most businesses think those plans now seem too aggressive, said Forrester analyst Benjamin Gray.
While corporate technology departments are looking forward to some of Vista’s security features and easier administration tools, there’s little reason to switch if the more secure PCs end up choking on a critical piece of software.
"They’re waiting for Microsoft to bless it with a service pack," said Gray, referring to a major software update that fixes bugs.
To me, though, the interesting part of the story concerns the usability of the new security features:
One of the most common annoyances: Microsoft’s user account control feature, designed to protect unwitting Web surfers from spyware and viruses that would otherwise install themselves on the computer.Anyone who has used Vista knows exactly what he’s talking about: there are lots of pop-ups, asking you to confirm that you really intended some particular action. Going forward, I don’t think this is a viable approach; people won’t put up with it. But is there an alternative?Dan Cohen, chief executive officer of Silicon Valley startup Pageflakes, bought a Vista laptop a couple of months ago. After one too many pop-up windows warning of possible threats from the Internet, Cohen switched the control feature off.
Now he gets pop-ups warning him that turning off UAC is dangerous.
"I feel more secure — and more irritated," he said.
Some of the pop-ups are occur when you try to do something that’s inherently privileged, such as installing a new device driver. Unix and Linux users have long been familiar with this, and they know to use su or sudo prior to issuing such commands. Other things, though, are extra protections against what had been unprivileged operations, such as specifying that certain programs should be executed at log-in time. On Windows, this could be done simply by copying the program to the Start Up folder; on Unix and Linux, it simply involves editing .profile or the like. However, this is now an operation that requires confirmation — and rightly so, because viruses and worms have long exploited this feature (or the registry-based equivalent) in order to restart at reboot time.
But there’s a major downside: we’re in a situation where users are routinely prompted to click "Yes", often to deal with threats they don’t understand. You have to click "Yes" to protecting yourself, but if people are habituated to click "Yes" frequently, the protective effect of Windows Vista will be gutted.
In fact, it’s worse than that. Many new machines come preloaded with what Walter Mossberg of the Wall Street Journal calls "craplets". These are trial and advertising applications, and it isn’t always obvious how to make them go away. For example, on my new Vista/Ubuntu box, I had to delete some vendor-supplied desktop clutter asking me to subscribe to some photo site. (Perhaps I’ll name the vendor in another post…) A few days later, though, I received a pop-up asking me again to subscribe. And shortly after that, I was asked to permit some vendor-supplied application to update itself. Should I do this?
The Vista pop-ups warn you not to say "yes" unless it’s an action you initiated. Fair enough, and I assume I’d see the Vista pop-up if I permitted the vendor software upgrade to continue. But where did that come from? Is it really software that was on my machine, out of the box, and hence no less (and no more) trustworthy than the rest of the preloaded software? Not that that’s a ringing endorsement — I may be letting myself in for a new round of solicitations for photo sites or auction sites or the rest of the annoyances I hope I’ve deleted — but what if the update request was from piece of malware I’d somehow acquired? How do I know what I’m consenting to?
Microsoft is in a very difficult position here. Explicit permission before dangerous operations are performed is clearly necessary. On the other hand, the frequency of the permission requests and the lack of clarity about what will actually be done pose a usability (and hence a security) challenge. Consider this request for permission when I asked Windows to delete a program:
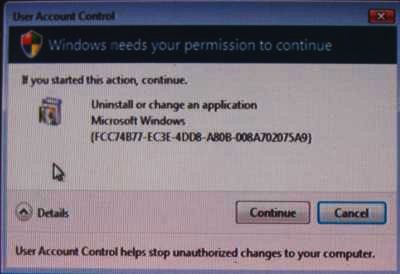
Anyone want to tell me exactly what it is I’m being asked to consent to? What program is being uninstalled or changed (and which is it)?
Mind you, I’m not blaming Microsoft. While some of the security usability woes of Vista are undoubtedly due to the need for backwards compatibility with their older, horribly insecure operating systems, others — like this example — are inherent in the problem. The real question is what to do. As I’ve often remarked, if we knew the answer it wouldn’t be research.
