- Kernel sources have already been installed in your VM in /usr/src/linux-2.6.11.12.tar.gz.
You will use these
sources for
building the kernel. As far as building the kernel is concerned, it
doesn't actually matter where you put the sources; the default
location is /usr/src:
$ cd /usr/src
We recommend that you keep a backup of everything that you write or modify outside your assigned VM, e.g. in your home directory. The data in the VMs is
$ tar -xzvf [path-to-tar-file]/linux-2.6.11.12.tar.gznot backed up . Thus, should your VM crash its disk, your sources will still be available.
The Linux version you are using utilizes a newer assembler than the one originally available to compile the Linux Kernel 2.6.11. Because of this you must apply a patch to the linux source code before compiling. Please be aware that this is not typically the case!!
-
cd /usr/src/linux-2.6.11.12/
-
patch -p1 < ../linux-2.6-seg-5.patch
-
- The source will extract into a directory called linux-2.6.11.12
(for a version 2.6.11.12 kernel). Don't touch this directory! As we'll
see, it's useful to have a copy of the pristine sources lying around.
Instead, make a copy with the command ``cp -al linux-2.6.11.12
linux-2.6.11.12-pudding'', replacing pudding with the
desired suffix that will uniquely identifies your kernel, such as "-hmwk2".
The -al flags to cp make the copied tree use
all hard links instead of full copies of files. What does this mean?
Run ``du linux-2.6.11.12'', then ``du -c
linux-2.6.11.12
linux-2.6.11.12-pudding''. One tree takes up 268 MB, but two
trees together take up 273 MB! The extra 5 MB go to the directories
themselves, which can't be hardlinked (think about why this is). You
can now make all your changes to the copy. Since you will generally
only change a few files in the kernel, this is a big win in terms of
disk space when keeping around multiple slightly different source
trees.
A little care is needed to make sure the linked files are copied when written. If you use emacs to edit, you should have no problem: when you first make a change to a file in emacs, it moves the original file link to a backup (the ~ file), and makes a copy to work on. Likewise, the patch program moves the original link out of the way and makes a copy before patching a file. However, IF YOU USE VI, YOU WILL HAVE TO RUN ``mv file file~; cp file~ file'' BEFORE YOU START EDITING. Yes, this may seem like a pain in the neck right now, but you'll be glad for the time saved:
$ time cp -a linux-2.6.11.12 linux-2.6.11.12-realcopy
real 0m41.476s user 0m0.140s sys 0m3.340s
$ time cp -al linux-2.6.11.12 linux-2.6.11.12-linkcopy
real 0m0.428s user 0m0.030s sys 0m0.400sThen, say I make some changes to the copies, and want to make a diff with the original sources (more about this later):
$ time diff -Naur linux-2.6.11.12 linux-2.6.11.12-realcopy > /tmp/patch1
real 0m2.615s user 0m1.250s sys 0m1.360s
$ time diff -Naur linux-2.6.11.12 linux-2.6.11.12-linkcopy > /tmp/patch2
real 0m0.278s user 0m0.160s sys 0m0.120s - Compiling the Kernel
To compile the kernel so that it recognizes your hardware, you need to set up a config file. You can find a sample config file in your VM at /usr/src/w4118_2.6.11.12.config that you may use within the vmware environment. This config file is confirmed to work with your recently downloaded kernel version, as well as with the patched one you will be building for part 2 of this assignment. In order to use this config file, simply copy it to .config in the toplevel of your source tree and type make oldconfig. The kernel should configure itself without any input necessary on your part. - You can alter the configuration options of the kernel by running make menuconfig. In particular, one useful option is the "General setup ---> Local version" option: a string that is appended to kernel release, and can be used to identify your kernel. For instance, you may change the local version to ".hmwk2" for homework#2.
- Once the kernel is compiled, you must install the new boot
image and
tell the boot manager where to find it. To install a new kernel, do:
$ make install
On the first time that you install a new kernel, and everytime you make changes that may affect modules (e.g. modifying an important include file) you also need to install the modules. It is also recommended to update the vmware-tools to match the new kernel. Assuming that your kernel version suffix is ".hmwk2", you can do these by:$ make modules_install
To let the bootloader, grub, know where to find your kernel, be sure to enter the appropriate information into your /boot/grub/menu.lst file. You can create a new entry by copying an existing one (e.g. that of linux-2.6.11.12-base) and changing all instances of the kernel version to 2.6.11.12.hmwk2, for example:
[edit /boot/grub/menu.lst]
[reboot with new kernel]
$ vmware-config-tools.pl
title Ubuntu, kernel 2.6.11.12.hmwk2
root (hd0,0)
kernel /boot/vmlinuz-2.6.11.12.hmwk2 root=/dev/sda1 ro
savedefault
NOTES:- The kernel image should be placed in /boot. It is listed as /vmlinuz-2.6.11.12.hmwk2 above because grub treats paths as relative to /boot.
- Unlike lilo, there is no need to run a program when you
change the configuration file or recompile the kernel. As long as there
is an entry for the kernel image in /boot/grub/menu.lst, grub will
recognize it.
Note that you will be adding this system call to the kernel based on the 2.6.11.12 kernel you previously built with kernel debugging installed. For the following discussion all relative paths refer to the top of your kernel source directory. For example, if your kernel is located in /usr/src/linux-2.6.11.12.hmwk2 then the relative path include/linux/types.h refers to the file /usr/src/linux-2.6.11.12.hmwk2/include/linux/types.h.
The system call you write should take two arguments: int enable to enable and disable logging for the current process, int max_entries to define the number of system calls to record, and return an integer describing whether the operation was successful or not. As a side-effect, it will trigger a syscall-logger (described below) for the current process. The system call number must be 289. The prototype for this system call is:
int setrecording(int enable, int max_entries);Be aware that kernel resources are limited and memory should not be plainly allocated as in user-mode. So, we will pre-define a global maximum of 4000 entries in the system you should verify this global maximum against int max_entries in the setrecording system call. You will only record up to the first 'max_entries'.
Your second system call will be used to retrieve the information stored in the kernel, it should take two arguments: an array of log structures allocated by the user-application and the number of log structures you have allocated in user-land. The return value should be similar to the return value of read(): on success, the number of struct reclog copied is returned. It is not an error if this number is smaller than the number of struct reclog requested; this may happen because there are fewer struct reclog than requested such as when there is nothing to retrieve return 0. The system call number must be 290. The prototype for this system call is:
int getrecording(struct reclog *log, int nr_logs);Once this function finishes, struct reclog *log will have an array of ordered system calls. NOTE that you are still recording until you call setrecording to disabled the syscall-logger. For example, if max_entries is 5, 5 system calls were recorded, and nr_logs was 3, you should now have room to record 3 more system calls.
Define
struct reclog asstruct reclog {
long syscall_nr; /* system call number */
long arg1; /* arguments of system call */
long arg2;
long arg3;
long arg4;
long arg5;
long arg6;
};
in include/linux/recinfo.h as part of your solution. You should also be able to #include it as part of a user-land application (see prob. 4).
Your code should handle all errors that can occur. At a minimum, your system call should detect and report the following error conditions:- -EINVAL: if log is null
- -EFAULT: if log is outside the accessible address
space.
Syscall-logger: System
calls are implemented as traps or software-interrupts that transfer
control to a specific kernel code, Linux has registered software
interrupt 0x80 in the interrupt descriptor table for invoking system
calls. Utilizing the %eax register as the index into the sys_call_table
in arch/i386/kernel/entry.S the system
call handler jumps to the specific code in the kernel for that
system function.
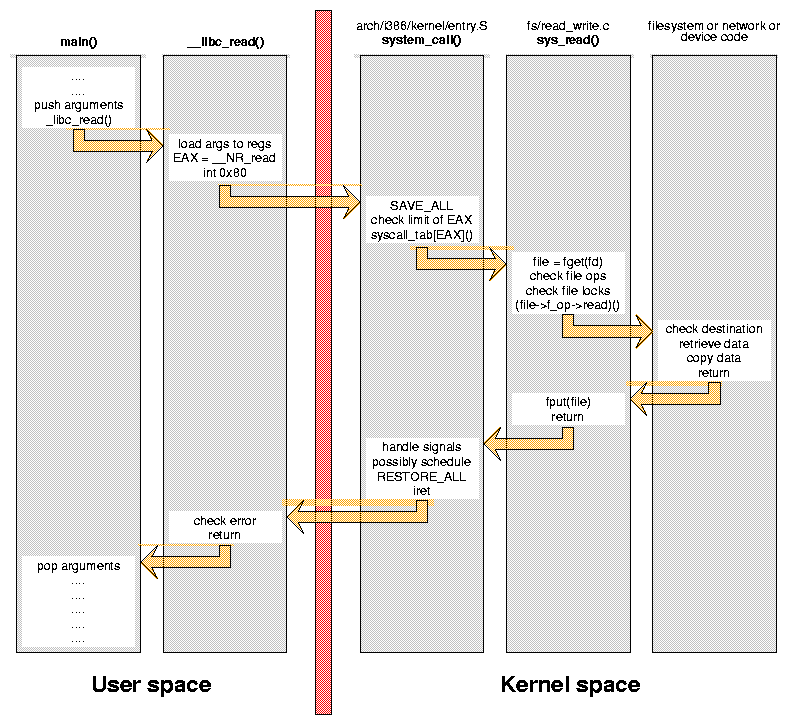
You will add to arch/i386/kernel/entry.S the following
assembly code
provided to create the system call logger. Line numbers are clearly
indicated where they should be added (251-267 or with KDB patch 263-279):
250 syscall_call:
251 pushl %eax
# pushad is the ISA standard
252 pushl %esp
253 pushl %ebp
254 pushl %edi
255 pushl %esi
256 pushl %edx
257 pushl %ecx
258 pushl %ebx
259 call
record_syscall #
HW2: SYSCALL LOGGER FUNCTION
260 popl %ebx
261 popl %ecx
262 popl %edx
263 popl %esi
264 popl %edi
265 popl %ebp
266 popl %esp
267 popl %eax
268 call
*sys_call_table(,%eax,4)
269 movl
%eax,EAX(%esp)
# store the return value
270 syscall_exit:
Create the function record_syscall() store it
in arch/i386/kernel/sysrecord.c
you must add sysrecord.c
to the correct compilation directive in the
Makefile.
asmlinkage void record_syscall(long arg1, long arg2, long arg3, long arg4, long arg5, long arg6);The above call will record information on the arguments given to the original system call, but be aware that the system call number is not in the parameters it must be fetched from the %eax register with the following code (must be the first instruction executed in function):
long index;
__asm__("movl %%eax, %0;" : "=r"(index) ); /* Save EAX into 'index' */
Additionally record_syscall() should maintain struct
kern_reclog in a linked list constructed using the kernel list
structures in include/linux/list.h:
struct kern_reclog {
long syscall_nr; /* system call number */
long arg1; /* arguments of system call */
long arg2;
long arg3;
long arg4;
long arg5;
long arg6;
... /* free to use structures to maintain this information */
};
This structure will be dynamically
allocated when record_syscall() is called and will be free'd
in getrecording() once
they've been copied over to the user buffer.
- Place your struct
kern_reclog structures is in the task_struct (Refer
to Chp. 3 p. 81 of Underst. Linux Kernel for information on the process
structure 'task_struct') of the current process. This can be
achieved by appending struct list_head reclist to the task_struct. (Refer
to Appendix A of Linux Kernel Development by Robert Love OR Underst.
Linux Kernel p. 87).
- Remember that we are only interested in recording information for the current process that executed the setrecording system call, thus you will have to store some information that uniquely identifies the process.
- On some occasions the process can die suddenly due to some
fault and if you do not clean the struct
kern_reclog of the process you will be leaking memory. You must
handle this by creating a cleaning function void
exit_reclog(struct task_struct *tsk) which you will call through the
predefined void free_task(struct task_struct *tsk).
Your submission should be a kernel patch off of the Linux kernel with
KDB that you created in the previous problem. A
patch is used to store changes you've made to the kernel and to submit
your
changes for this problem. For example, if you've changed 50 lines of
code, a patch
will be about 50 lines long. This is much easier to store, email, or
move around than the full 283,000-line source tree. To create a
patch, first back up your .config file, then do a ``make distclean''
in your changed source tree (you don't want object files, config
files, etc. in your patch). Then, from the directory above your source
tree (e.g. /vmware1/src), run
diff -ruN linux-2.6.11.12 linux-2.6.11.12-changed > changed.patch
Notice that the original source tree is first, and the one containing
your modifications is second.
There is a particular ``algebra'' to patches. You may find it
helpful to think of diff as subtracting two source trees. The
result of this subtraction is a patch. To apply a patch, then,
is to add this difference back. If you supply the -R
option to the patch program, you subtract the difference,
instead of adding. If you thus ``subtract the difference'' from
your changed tree, you end up with the original tree. So, to
contain all the information of n kernel trees, all
you need is the n - 1 patches between them, and only
one full kernel tree (and it can be any one of the n).
Big Hint: In order to learn about system calls, you may also find
it helpful to
search the Linux Kernel for other system calls and see how they are
defined. The file kernel/timer.c might give some useful
examples of this. The getpid and getuid
system calls might be useful starting points. The system call
sys_getpid defined in kernel/timer.c uses current
macro and
provides a good reference point to how you should define
your
system call.
- Enable the systemcall-logger
- Call some system calls: any number of system calls you want. Verify this with the linux command strace.
- Disable the systemcall-logger
- Retrieve the logged entries
e.g:
user> test-record
Calling setrecording(1)...
Calling some system calls to log:
Testing printf()
Testing open()
Testing close()
Calling setrecording(0)...
Calling getrecording()... SUCCESS
-------------------------------
Here is the list of calls made:
...
N. __NR_[289] (0, 5, 123, -1207956256, 0, -831438848)
...
...
...
...
...