
Consumers are now paying close attention to how companies behave and treat consumers during this global COVID-19 public health crisis.
Rest assured, when this crisis is behind us, consumers will be much more thoughtful about where they spend their money, especially if dealing with the aftermath of identity theft caused by COVID-19-themed phishing campaigns.
Who will customers blame? Most likely, the companies whose websites were spoofed to trick them into giving up their personal information.
Companies' typical response to thwart phishing is to warn their customers to be more vigilant to spot phishing emails on their own.
Why don't those companies take more responsibility to protect their brand from misuse by phishers? Why won't they fight back by making phishing unprofitable? They have the means to do so.
What's most egregious about brands blaming their customers for falling prey to phishing attacks is that the customer was lured by their trust of that brand.
Advances in technology make it easier than ever for malicious actors to build a spoof site.
Just as new technology has produced "deep fake" videos, the new generation of spoof websites are making it harder to spot the suspicious sites, even to the trained eye of security professionals. And attackers are counting on a strong trust relationship between the customer and, for example, their bank. It's what gets the victim to be tricked into clicking.
Preying on pandemic fear
Phishing has become the preferred method of social engineering attack, commonly used to steal user data such as login credentials and credit card numbers. The attacker masquerades as a trusted entity, such as the victim's bank or place of employment.
First, the attacker builds a highly convincing fake website, modeled after a brand the victim knows and trusts. Often, the attacker will use real images and text from the original website - a technique known as content scraping. It's remarkably simple for an attacker to make a wholesale copy of the real site, and doctor it slightly. Once the fake domain is launched, the attacker next dupes the victim into opening an email, instant message, or text message containing a link to that spoof site.
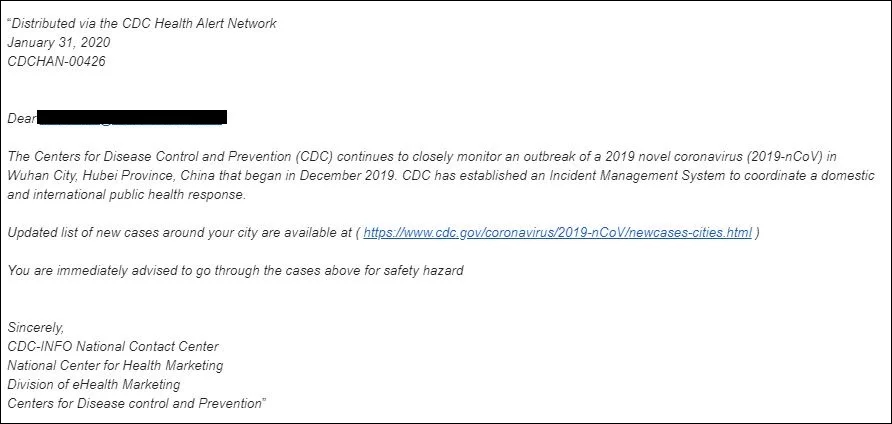
Under normal circumstances, the victim is lured by the trust of the brand being impersonated. But the motivation has taken a disturbing turn since the beginning of the pandemic. Attackers are now masquerading as government agencies, luring consumers using messages about the spread of COVID-19.
In this example, the cybercriminal sends an email that appears to originate from the Centers for Disease Control (CDC), urging the victim to click on a link for an "updated list of new cases" in their area.
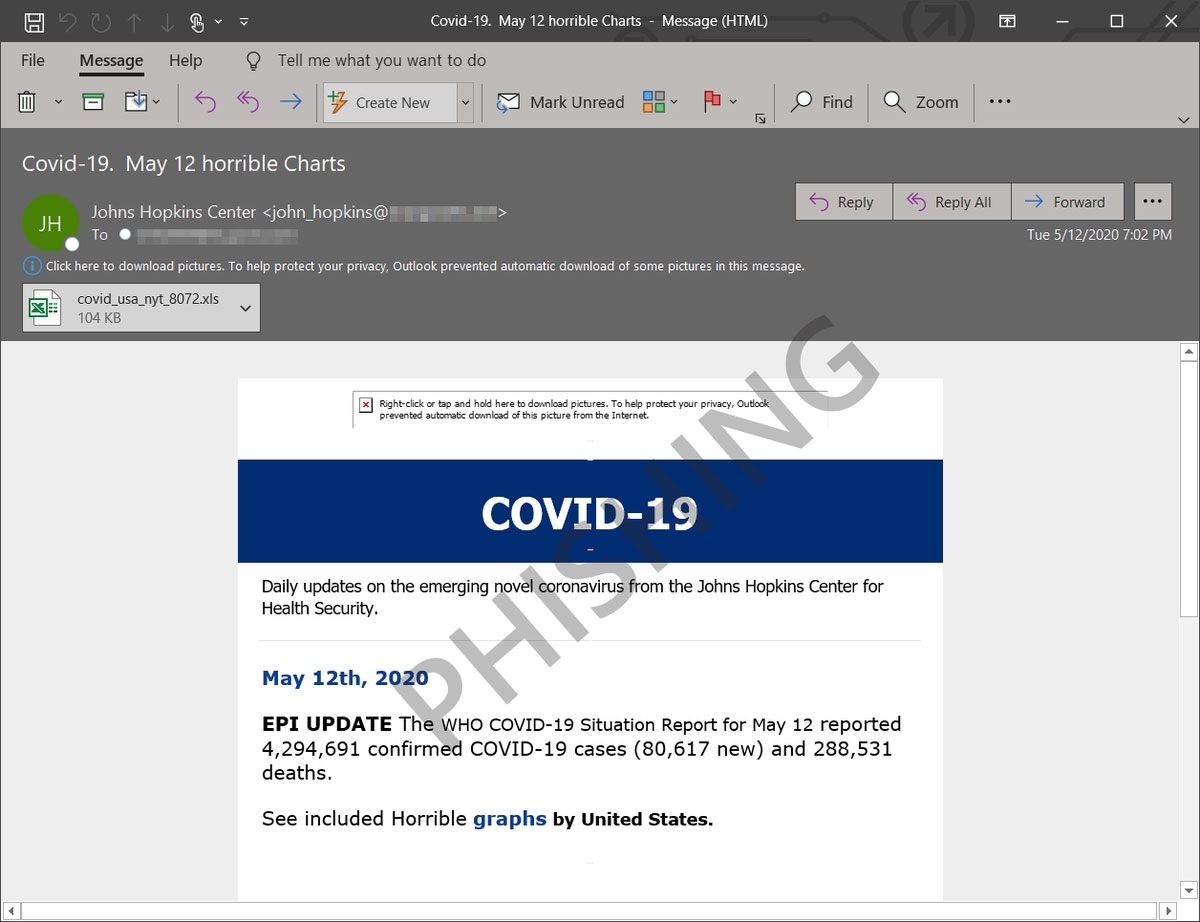
Another attack specifically targeted the users of Microsoft email products using an email appearing to come from John Hopkins Center, claiming to share news on the number of Coronavirus-related deaths.
It's easy to see why these attacks are successful. As citizens grow more concerned and seek reliable information about the spread of the coronavirus, messages like these are hard to resist. And the phisher is relying on that.
Cybercriminals are leveraging fear to make a profit, and it's time for brands to stop letting them get away with it.
In an age in which data breaches are rampant, customers are increasingly fed up and demanding justice from brands who didn't take the right precautions to protect customer data. Why should consumers continue to spend money with businesses that don't do everything in their power to protect their data and privacy?
Turn the tables on the attackers
With disclosures of phishing attacks increasing each year, we can conclude that most of the anti-phishing tools in the enterprise aren't getting the job done. When some "solution" fails to work, doesn't it make sense to try something else that does work?
A better way to approach detection is to beat the attackers at their own game. Catch them in the act before they have the opportunity to get away with their scam.
Using undetectable lines of code that are embedded into the design of a corporate website, for example, could help defenders know when that website has been scraped for content. The code serves as an alarm of sorts when this activity is in motion as a site's content being scraped is an early red flag that they are being targeted.
The technology to make this happen already exists, and web security personnel in any company can protect their site and brand with this early warning technology.
Once defenders are aware of the potentially fake website, they could take a couple of different paths on mitigation.
Defenders can approach the service provider hosting the phony site and request that it be taken down. It's also possible to leverage the fake site against the attacker.
This would involve flooding the fake website with phony credentials or decoys. To the attacker, it will appear that scores of unwitting consumers are visiting the site and entering their login information. Using a touch of deception has the potential to create doubt on the fraudster's part about what may have been stolen, whether it is real or fake.
This is the time for companies to put their customers first and finally make phishing a more risky and unprofitable exercise for hackers. It's especially evil of cybercriminals to exploit the fear and uncertainty of a global pandemic to steal information and invade citizens' privacy.
By investing in modern security that will finally address phishing at its core, companies are going above and beyond for their customers and protecting their reputation and bottom line.
It's time to turn the tables on adversaries and make them pay the price for using the trust between a brand and its customers as a weapon.


Comments
MrCBax - 3 years ago
I have been working on a project for this type of offensive security for a while. Here is the repo: https://github.com/LogoiLab/ActiveAntiPhish
This article reads eerily similar to my blog post: https://computeco.de/posts/2019-06-16_1.html
Sal2020 - 3 years ago
Excellent. I've been working on this for over a decade. Perhaps you might find this article of interest?
Brian Bowen, Pratap Prabhu, Vasileios P. Kemerlis, Stelios Sidiroglou, Angelos D. Keromytis, Salvatore J. Stolfo; "BotSwindler: Tamper Resistant Injection of Believable Decoys in VM-Based Hosts for Crimeware Detection;" Proceedings of the 13th International Symposium on Recent Advances in Intrusion Detection (RAID); 2010/09. PDF: http://ids.cs.columbia.edu/sites/default/files/VMInject_RAID2010.pdf
It might be cool to work on this avenue collaboratively.
DyingCrow - 3 years ago
I used to spam fishing sites with fake credentials, years ago, mostly stuff straight off urban dictionary. Believe it or not, i got at least ONE email asking me to stop. Maybe they didn't know how to block me or something. Or maybe i really pissed them off with so much clutter.
Unfortunately, that 28 year old hotmail account- which i used in a campaign to sign up on every shady website i could come across, and "others", to get as much traffic as possible - is but an old road, now. Maybe M$ really stepped up their spam filters, or something, or maybe because the focus is just not individuals anymore.
Sam Gunn - 3 years ago
I talk to tech support scammers on the. I talked to one guy for 31 minutes. He asked me to type doblu doblu doblu dot, and the web address. So I typed dobludobludobludot, and the web address. It said that the page could be displayed. And that's what I told him. He asked me to type it again, and I did. It said the same thing. And that's what I told him.
In the end, he told me that hackers from Alabama are trying to hack into my computers.
Now Alabama does have some smart people. But I don't think any of them were trying to hack in my computer.
I also talk to card services scammers.